What is GRC?
GRC is an acronym for Governance, Risk, and Compliance. There are several ways in which GRC can be defined and every organization shapes its GRC strategy based on internal business objectives, government regulations and industry standards. At its core, GRC involves managing the four major components of any organization:
People:
People includes resources who define, perform, monitor, manage, govern, assess, audit, etc.
Process:
Processes enable standardization, greater efficiency, and control via policies that define what is to be done and procedures that define how it is to be done. Processes also facilitate the proactive identification and avoidance of potential risk and threats, continuous monitoring, and reporting of progress.
Technology:
Technology enables a common data repository, advanced automation (workflow, notification, processes, etc.), analytics, improved efficiency and effectiveness, and greater productivity leading to significant cost savings, and improved performance metrics.
Data:
Data is the information that is utilized to monitor, control, and make GRC decisions
What is GRC Used For?
GRC provides a structured approach to achieve governance, manage organizational risk and ensure compliance with regulations. GRC helps organizations align their IT with business objectives while effectively establishing best practices, managing IT and financial risks, improving decision-making, controlling costs, reducing silos, and acting with integrity.
The Three Pillars of GRC
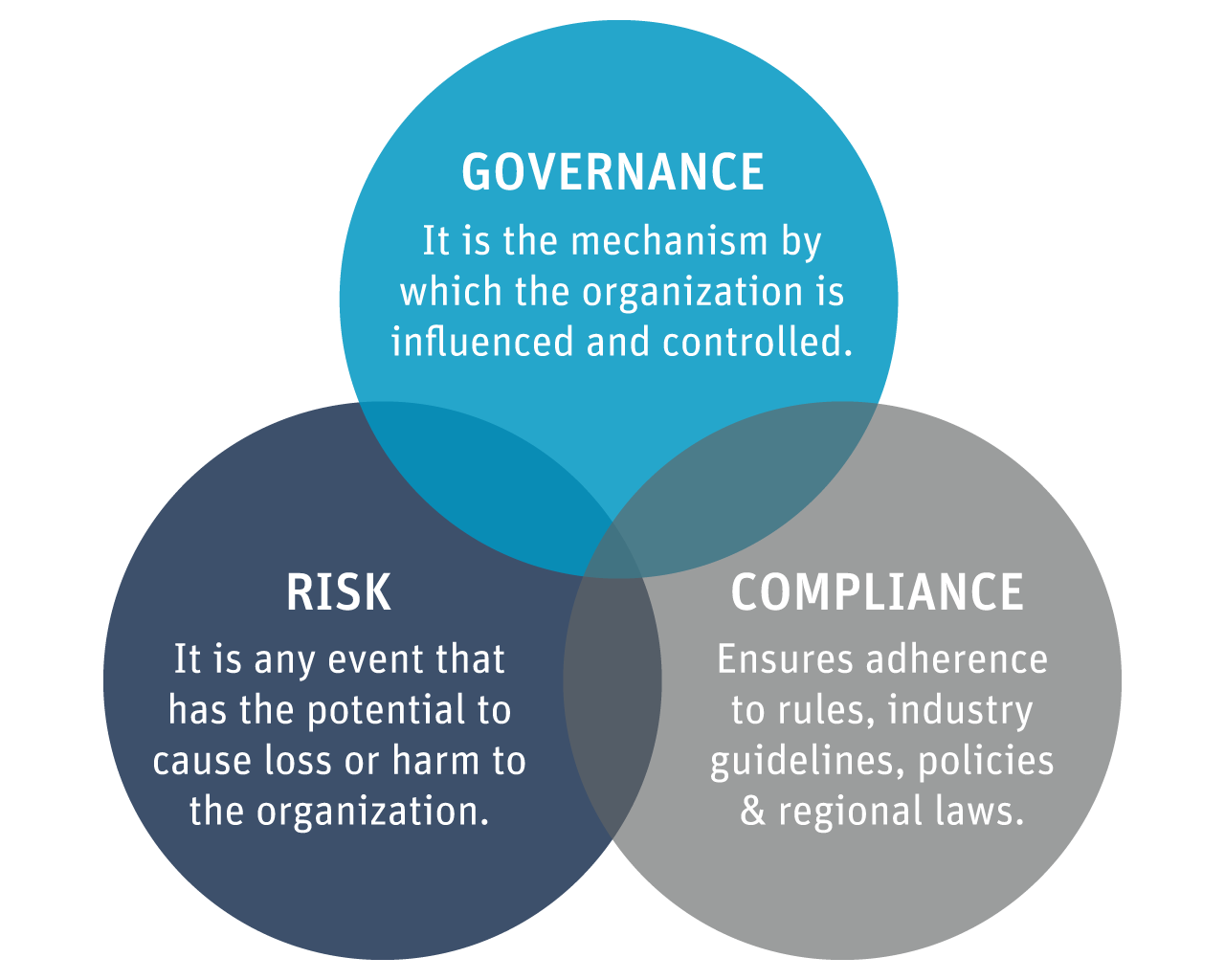
Governance: It is the mechanism by which top management can direct and influence the organization across all levels. Governance involves orchestrating rules, policies, processes, and controls that ensure the alignment of corporate objectives with the organization’s business goals.
Risk Management: Risk is any event that has the potential to cause loss or harm to the organization. In the context of GRC, risk management requires the identification, assessment, and control of legal, strategic, financial, and security risk to an organization.
Compliance: The goal of compliance in GRC is to ensure that the organization adheres to a standard or set of rules, industry guidelines, policies, and regional laws that are mandated by the respective industries and/or government agencies. For IT, this translates to protection of data and ensuring authorized access to data.
How GRC Affects ERP Applications
ERP applications are used across industries and global business operations to store and access a variety of data. This data includes both personally identifiable information (PII) and sensitive information like financial data and intellectual property. This makes is essential, and in many cases mandatory, for organizations to protect the integrity and govern access to ERP data.
With compliance and data privacy regulations imposing greater control over who accesses what data, businesses are struggling to continuously monitor user activity inside ERP applications. One of the reasons being the lack of internal controls within ERP applications. Most ERPs offer role-based access which allows users unrestricted access once they have logged into the system.
However, the role-based access model neither considers the context of access, nor does it allow you to implement adaptive security controls. To effectively implement access governance, organizations need to adopt policy-based access controls and solutions that restrict access to data based on the inherent risk exposure.
Drivers for GRC
Privacy and Fraud
The increase in interconnectedness and the rising value of data has created a complex security and risk landscape for all businesses. As governments and private citizens are becoming more concerned over how their data and money is collected, stored, accessed, and used, several regulatory compliance mandates are emerging. The burden of ensuring that these mandates are met falls on the shoulders of top management.
Security Threats
Compliance apart, businesses also need to protect data and intellectual property from insider threats and a slew of external threats who are constantly finding new ways to circumvent the existing security infrastructure.
Digital Transformation
Additionally, the growing complexity of the business and IT landscape which needs to operate across multiple ERP applications that connect employees and third-party vendors is making it difficult to implement policies, manage risk and adhere to compliance requirements consistently.
Privacy and Fraud
The increase in interconnectedness and the rising value of data has created a complex security and risk landscape for all businesses. As governments and private citizens are becoming more concerned over how their data and money is collected, stored, accessed, and used, several regulatory compliance mandates are emerging. The burden of ensuring that these mandates are met falls on the shoulders of top management.
Security Threats
Compliance apart, businesses also need to protect data and intellectual property from insider threats and a slew of external threats who are constantly finding new ways to circumvent the existing security infrastructure.
Digital Transformation
Additionally, the growing complexity of the business and IT landscape which needs to operate across multiple ERP applications that connect employees and third-party vendors is making it difficult to implement policies, manage risk and adhere to compliance requirements consistently.
GRC Challenges in ERP Applications
SoD Compliance
Organizations that rely on spreadsheets to track and maintain roles and authorizations struggle with slow, inefficient, and error-prone processes. In addition, this approach is not scalable as employees’ roles and duties change, and the organization grows in size and complexity over time. Spreadsheets also lack audit trails and actionable insights, potentially causing any unresolved SoD conflicts to negatively impact audit reports and compliance with the Sarbanes Oxley Act (SOX) and GDPR.
Appsian Security provides a single control point to manage and enforce segregation of duties (SoD) across multiple ERP platforms. This full-suite solution includes SoD rules definition, conflict analysis & resolution, real-time violation prevention, and detailed incident analysis. This capability helps to prevent SoD conflicts in real-time before they occur.
Data Security & Privacy Compliance
Traditional data security controls fail to protect sensitive data at the field level leading to unnecessary data exposure. Moreover, ERPs provide limited data privacy controls and logging capabilities that only focus on who logs into and out of the system while failing to track who is accessing sensitive data. Also, since most user access policies are based on static roles, there is a high risk of data exposure and misconfigurations leading to data privacy compliance violations.
Appsian Security can limit sensitive data exposure by enforcing full or partial data masking in the ERP user interface at the field level. Furthermore, Appsian provides granular visibility into the who, when, and where of data access and usage. With pre-built reports for GDPR and CCPA, Appsian can ease data privacy compliance management. These ready-to-use reports help respond to audit challenges promptly and contain data breaches faster.
Mitigation of Data and Transaction Risk
Enterprises do not continuously monitor employees and third-party service providers to analyze SoD violations, master data modifications, and transaction-level activities. Instead, only a random fraction of high-risk activities are monitored during periodic audits. As a result, there can be strategic, financial, operational, contractual, credit, compliance, business continuity, and reputational risks that stay undetected across your ERP deployment.
Appsian helps provide real-time, context-based monitoring within your ERP deployment at the access, transaction, and data level to enable you to be audit-ready. In addition, the solution offers comprehensive monitoring 24/7, 365 days a year of high-risk activities carried out by employees and third-party users. This level of monitoring helps rapid detection of violations, reduce their impact, and achieve a faster incident response.
Assessment of Access Risk
The manual access risk assessment process provides the lowest level of operating efficiency. And while an automated assessment process is more efficient, it is still dependent upon the security administrators to manually analyze the results, identify vulnerabilities, and determine corrective action.
Appsian’s AI & ML empowered continuous access risk assessment and recommendation engine provides the highest level of access management operating efficiency. As a result, organizations can realize dramatically lower operating costs by reducing human interaction in the access risk assessment, impact analysis, and recommendation steps.
SoD Compliance
Organizations that rely on spreadsheets to track and maintain roles and authorizations struggle with slow, inefficient, and error-prone processes. In addition, this approach is not scalable as employees’ roles and duties change, and the organization grows in size and complexity over time. Spreadsheets also lack audit trails and actionable insights, potentially causing any unresolved SoD conflicts to negatively impact audit reports and compliance with the Sarbanes Oxley Act (SOX) and GDPR.
Appsian Security provides a single control point to manage and enforce segregation of duties (SoD) across multiple ERP platforms. This full-suite solution includes SoD rules definition, conflict analysis & resolution, real-time violation prevention, and detailed incident analysis. This capability helps to prevent SoD conflicts in real-time before they occur.
Data Security & Privacy Compliance
Traditional data security controls fail to protect sensitive data at the field level leading to unnecessary data exposure. Moreover, ERPs provide limited data privacy controls and logging capabilities that only focus on who logs into and out of the system while failing to track who is accessing sensitive data. Also, since most user access policies are based on static roles, there is a high risk of data exposure and misconfigurations leading to data privacy compliance violations.
Appsian Security can limit sensitive data exposure by enforcing full or partial data masking in the ERP user interface at the field level. Furthermore, Appsian provides granular visibility into the who, when, and where of data access and usage. With pre-built reports for GDPR and CCPA, Appsian can ease data privacy compliance management. These ready-to-use reports help respond to audit challenges promptly and contain data breaches faster.
Mitigation of Data and Transaction Risk
Enterprises do not continuously monitor employees and third-party service providers to analyze SoD violations, master data modifications, and transaction-level activities. Instead, only a random fraction of high-risk activities are monitored during periodic audits. As a result, there can be strategic, financial, operational, contractual, credit, compliance, business continuity, and reputational risks that stay undetected across your ERP deployment.
Appsian helps provide real-time, context-based monitoring within your ERP deployment at the access, transaction, and data level to enable you to be audit-ready. In addition, the solution offers comprehensive monitoring 24/7, 365 days a year of high-risk activities carried out by employees and third-party users. This level of monitoring helps rapid detection of violations, reduce their impact, and achieve a faster incident response.
Assessment of Access Risk
The manual access risk assessment process provides the lowest level of operating efficiency. And while an automated assessment process is more efficient, it is still dependent upon the security administrators to manually analyze the results, identify vulnerabilities, and determine corrective action.
Appsian’s AI & ML empowered continuous access risk assessment and recommendation engine provides the highest level of access management operating efficiency. As a result, organizations can realize dramatically lower operating costs by reducing human interaction in the access risk assessment, impact analysis, and recommendation steps.
Enable GRC in your ERP Applications with Appsian
Many organizations struggle to manage employee access to their systems and data. The manual processes that are generally used to assess risk are time-consuming and audit only a small sample of critical GRC processes. The lack of continuous user activity monitoring, excessive authorizations (over-provisioning), and unresolved SoD conflicts eventually results in audit failures.
Appsian Security tackles each authorization-related decision from multiple angles, including financial risks, to help automate access management. The Appsian Security Platform’s embedded artificial intelligence (AI) and machine learning (ML) continuously identify potential risks and provide optimized suggestions for resolving user access risks, segregation of duties conflicts, and violations to compliance regulations while ensuring audit readiness.
In addition, it provides unprecedented visibility of real-time authorization usage, performs ongoing monitoring of every user, and sends alerts of any unusual or suspicious activity.